How do I import a CA certificate into my Hub Cloud instance?
Last Updated: | Applicable Hub Versions: Cloud
Last Updated: | Applicable Hub Versions: Cloud
Planview Hub Cloud does not allow importing CA certificates. However, in the event that you need to install a certificate in order for Hub Cloud to communicate with your repository, you can use a reverse proxy configuration to install your publicly signed certificate. For more details, see the sections below.
To import a CA certificate, you'll need to use a reverse proxy configuration (NGINX) where you can install both a publicly-signed certificate and your signing authority’s public certificate. The certificate should be locked down so that it can only be accessed by your Hub Cloud instance. This allows Hub Cloud to indirectly authenticate your On-prem instance without having to implement any security-breaking changes on Hub.
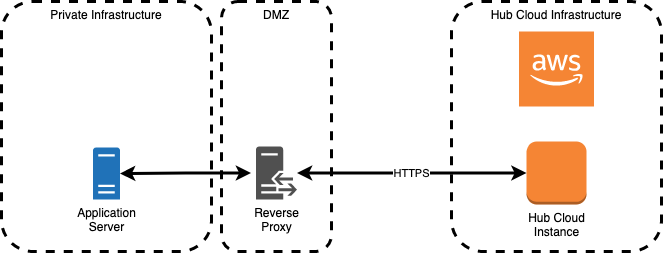
In the example below, the SSL proxy (Alpine+NGINX) is configured to forward traffic to an On-prem Jira deployment. The proxy then uses the publicly-signed certificate to authenticate the proxy to the Hub Cloud instance. Then, the CA certificate that signed the certificate used by Jira is copied into the container at build time.
upstream jira {
server jira:8080;
}
server {
listen 443 ssl;
server_name proxy;
ssl_certificate /etc/ssl/tasktop/certs/server.crt;
ssl_certificate_key /etc/ssl/tasktop/private/server.key;
location / {
proxy_pass https://jira/;
proxy_redirect http://jira:8080 /;
proxy_set_header Host jira;
proxy_set_header X-Forwarded-For jira:8080;
proxy_set_header X-Real-IP $remote_addr;
}
}
FROM nginx:stable-alpine COPY ./default.conf /etc/nginx/default.conf COPY ./ca.crt /usr/local/share/ca-certificates/ca.crt COPY ./server.crt /etc/ssl/tasktop/certs/server.crt COPY ./server.key /etc/ssl/tasktop/private/server.key RUN update-ca-certificates

