Tricentis Tosca
- Last updated
- Save as PDF

Overview
When your software engineering teams use Agile methods, requirements created by business analysts or user stories created by developers must flow easily to your QA team. This ensures that tests are written directly against these requirements or stories.
Connector Setup Details
This section describes the basic steps needed to prepare your Tricentis Tosca instance for use with Viz.
Minimal User Permissions & Viz User
We recommend that you create a new user within your external tool, to be used only for Viz. This is the user information you will enter when setting up your tool connection within Planview Viz. By creating a new user, you will ensure that the correct permissions are granted.
In general, your user account should have sufficient permissions to read artifacts in your tool.
Your user should have a secure password or token. Please be aware that Viz will not allow you to save a tool connection utilizing a weak password/token, such as 'tasktop.'
See instructions on how to create a new sync user in Tricentis Tosca.
List of minimal user permissions:
- Viz supports local workspace users only (LDAP users are not supported)
- User should be under the "Admins" user group to view/retrieve a list of users.
- User should have Set Result allowed enabled to set the execution results.
- User should have Level as "Expert" or "Advanced" to have read/write permissions on multiuser projects.
Note: The credentials you supply must be valid for every workspace you plan to include in your collection (in Hub) or query (in Sync).
Connecting to the Tricentis Tosca Repository
Standard Authentication
Required Fields:
- URL
- Example Format: http://abc-tosca223.van.server.com:8...ToscaCommander
- Username
- Password
- Please be aware that the “Successfully connected” response from Viz on the Tool Connection screen does NOT guarantee that Viz will be able to connect to the Tosca Workstation if the requirements listed above are not met.
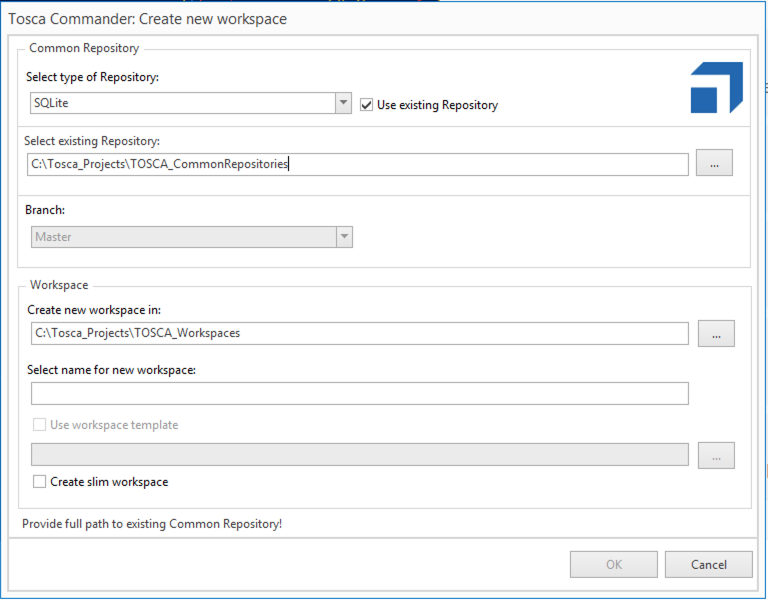
Note: As a general rule, Tosca Commander and Viz cannot be open and running at the same time, since both are using the same APIs. Therefore, to be able to synchronize with Tosca, you have to close your Tosca Commander workspace. However, a workaround is available:
- Prepare the database for multiuser mode by following instructions here.
- Create a new workspace and select your repository type under 'Common Repository' in 'Create New Workspace.'
- Create an additional workspace for your Viz instance. This time, ensure that you select 'Use existing Repository' under 'Common Repository' and select the Common Repository that you created in step 2.
- The workspace created in step 2 can be open while using Viz.
Personal Access Token with OAuth2.0 Proxy Authentication
Tricentis Tosca (Data Center): 15 and later
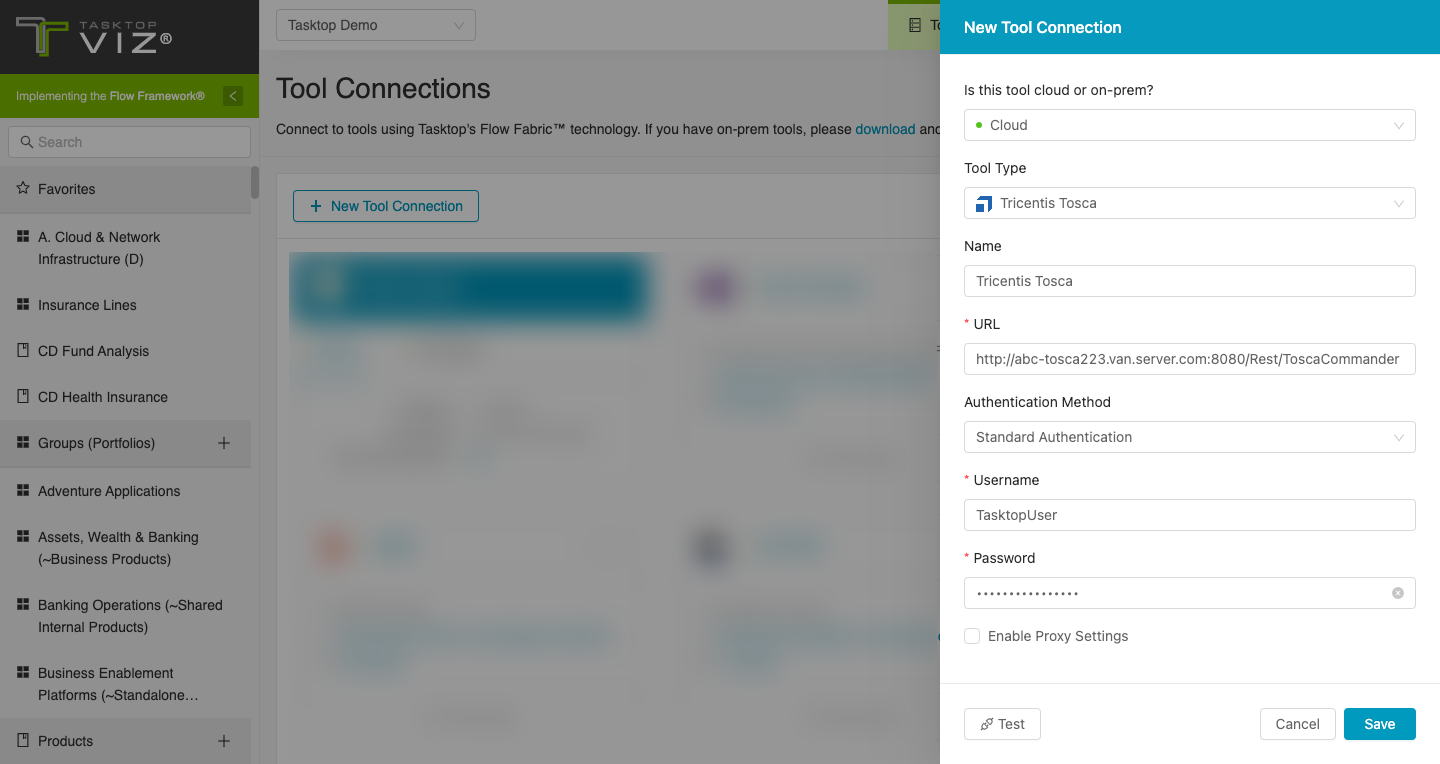
The Tosca connector supports proxy authentication using the OAuth 2.0 client credentials authentication flow to authenticate with the proxy through an identity provider, and using Personal Access Token authentication to authenticate with Tosca after the proxy.
Required Fields:
- Location/Proxy URL
- Example format: http://proxy-domain.com/proxy-path
- Identity Provider URL: Used to obtain the authentication token from the identity provider
- Client ID: A unique identifier assigned to a client application when it is registered with the identity provider
- Client Secret: Used to authenticate the identity of the client application when making requests to the identity provider
- Scope: Specify the access permissions
- Route: Based on the route, the request is redirected to the corresponding endpoint configured in the proxy
- Example:
Proxy URL: http://proxy-domain.com/proxy-path
Suppose the proxy is configured with the following route and corresponding redirection URL:Route
Redirection URL
Route123
Resource Path: /obj/1234
With this route configuration, upon successful authentication, the proxy will redirect the URL to: https://dev-tosca...com:8.../abc/obj/1234
- Example:
- Personal Access Token
- See details to learn how to create a personal access token in Tosca
Authentication and Routing Flow
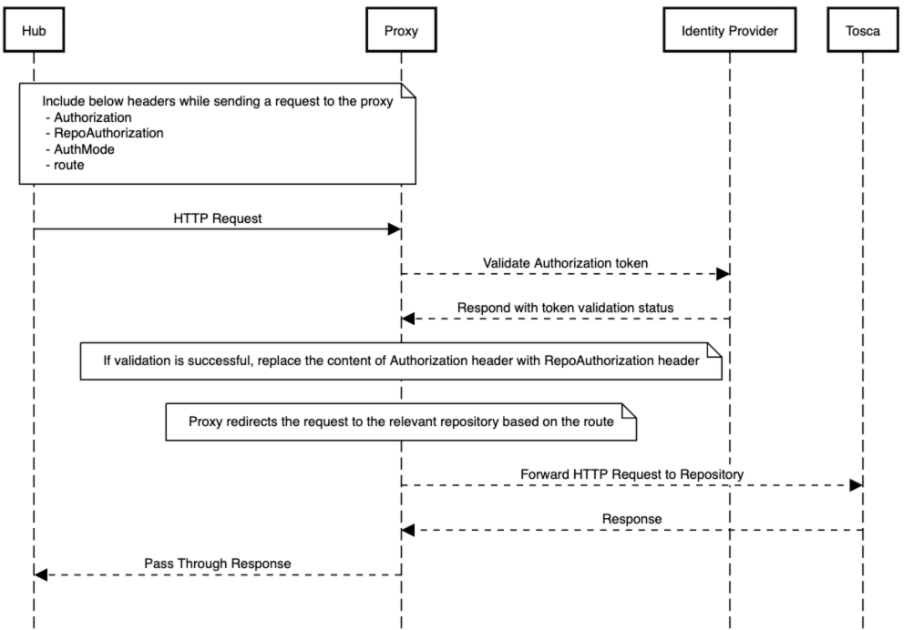
- HTTP Request Headers:
- Authorization: OAuth2 token obtained from the Identity Provider
- RepoAuthorization: Repository Token
- AuthMode: Set to "pat" (Personal Access Token)
- Route: Specify the route to the specific repository
- Proxy Authentication with Identity Provider:
- The proxy authenticates the OAuth2 token provided in the Authorization header with the Identity Provider, verifying its validity and checking for necessary permissions
- Validation and Redirection:
- Upon successful validation, the proxy replaces the content of the Authorization header with the RepoAuthorization token — this replacement is essential for redirecting the request to the repository, which requires the repository-specific token
- The route header specifies the destination repository for redirection
- If the validation process encounters an error, an error response is sent back to the client
Supported Artifacts
Supported Work Items
|
Supported Work Item Type |
Applicable Repository Versions |
Unique URL? |
|---|---|---|
|
Defect |
Supported versions including 9.2 and later |
No accessible web URL. Connector uses unique REST URI for location. |
Supported Containers
|
Containers that can be modeled as Flow Items |
Applicable Repository Versions |
Unique URL? |
|---|---|---|
|
N/A |
|
|
|
Containers used to define which artifacts are included in an Artifact Set |
|
|
|
Workspaces |
Any supported repository version: |
N/A
|
Supported Field Types
Planview Viz supports configuring rule-based modeling (i.e., conditional modeling) using the field types shown below.
Note: If one field of a given type is supported, others that are also that type in theory should also work. However, sometimes there are instances in which this is not the case due to the repository. So, while we can claim support for fields at the type level, there is a chance that some specific fields of a given type will not function properly.
|
Standard Field Type |
How is field type referenced in the repository? |
Sample Repository Fields Supported |
Particular Repository Fields NOT Supported |
|---|---|---|---|
|
|
String (Property) Date |
Name Change Request State Change Request Id Aggregated Description Comment Log Info |
|
|
|
|
Result Creation Container Workspace Type Container (Read Only) |
|
|
|
|
|
|
|
|
|
Changes Allowed Has Missing References |
|
Functional Limitations
|
Category |
Limitation |
Applicable Repository Versions |
|---|---|---|
| Third Party Functional Limitation |
Proxy Gateway Authentication Token-based authentication is applicable to Tosca Server-Based repositories. It's important to note that repositories like Multi-User Workspace do not support this and only allow username and password authentication. |
Tosca Data Center: 15 and later |
| Good to Know |
Proxy Gateway Authentication Tosca does not provide a distinct error code for an invalid token. Therefore, users may find it challenging to determine whether they have entered an incorrect token or if the token has expired. |
Tosca Data Center: 15 and later |