How does Viz connect to tools?
- Last updated
- Save as PDF
Last Updated: | Applicable Viz Versions: All
Answer
In Diagram A and Diagram B below we have outlined two different scenarios for connecting Planview Viz to cloud and on-prem tools. Please review the entire document, as Scenario A outlines details regarding the on-prem agent that are also relevant for Scenario B.
Scenario A: Cloud agent connects to cloud tools, on-prem agent connects to on-prem tools
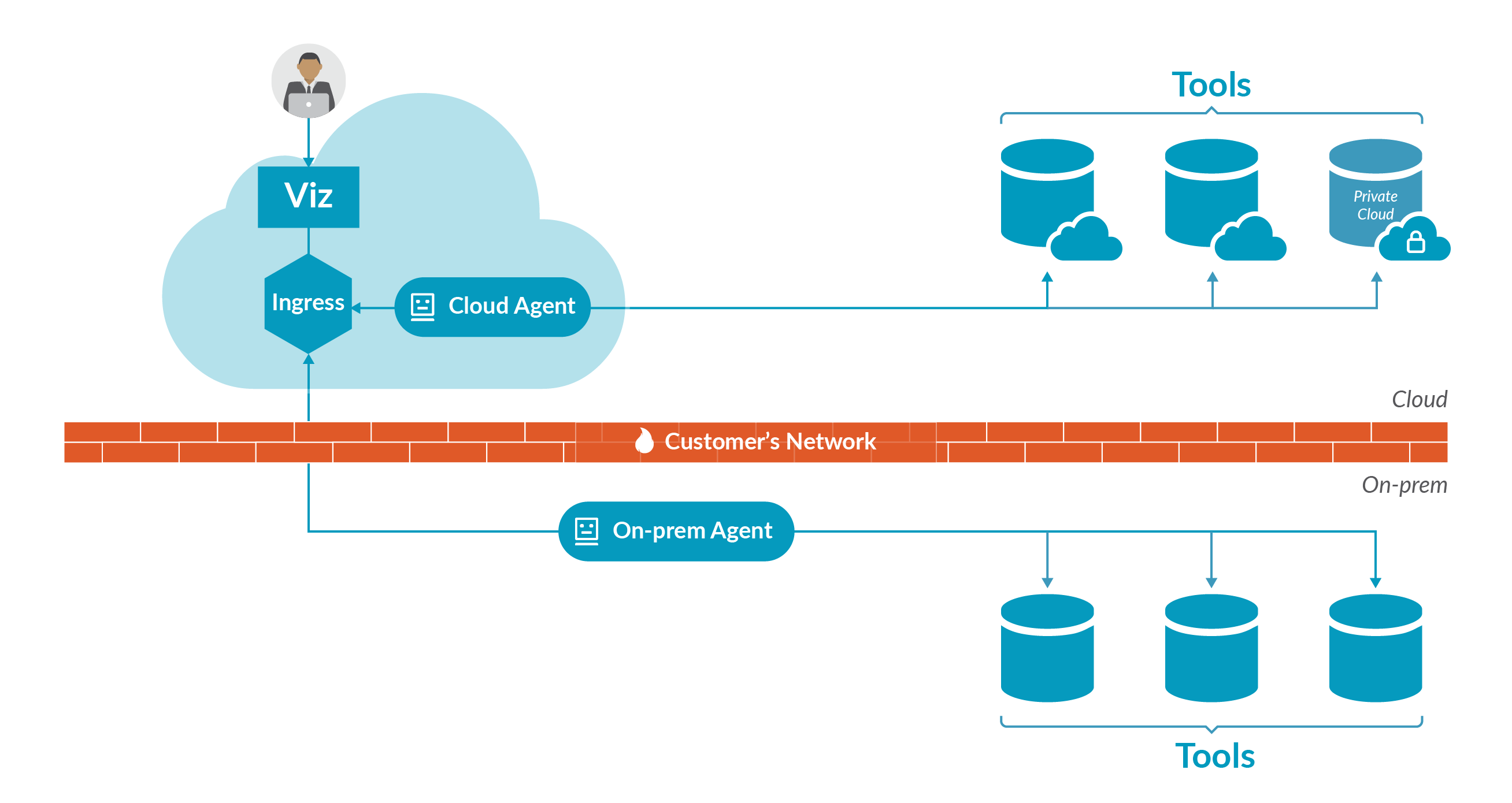
Diagram A above shows how Planview Viz connects to a variety of tools: on-prem, cloud, and within a customer's private cloud.
Note that the arrows in the diagram show the direction of how communication is initiated, and not the direction of data Flow.
Planview Viz is packaged with an on-prem agent that users can download and install. The agent allows Viz, a cloud product, to access data from on-prem tools, such as RTC or ALM.
The on-prem agent will need access to:
- https://ingress.viz.tasktop.net, in order to transport encrypted artifact events between on-prem tools and the Viz cloud. These events include:
- Configuration settings from Planview Viz, such as: tool connection credentials, artifact set configuration (list of projects and/or artifact sets to query in each tool), requests for agent health status
- Health information from the agent, such as: regular heartbeat pings, system diagnostics, tool connectivity health
- Artifact metadata from the agent, such as: fields and field values (for single- and multi-select fields) on eligible artifacts
- Artifact data from the agent identifying which artifacts have been detected as changed since the prior change detection
Users' personal computers will need access to:
- https://viz.tasktop.net, in order to access the Viz UI from a private network
Planview Viz is also bundled with a cloud agent. The cloud agent is available out-of-the-box, and does not need to be downloaded or installed. The cloud agent can connect to cloud tools, such as Jira cloud, and to tools within a customer's private cloud (behind a firewall).
If connecting to tools behind a firewall (private cloud/customer AWS) or to ServiceNow (which requires a list of accessible IPs input in the ServiceNow UI), the following cloud IPs must be whitelisted:
- 54.69.241.189
- 34.208.235.150
- 52.89.47.191
Scenario B: On-prem agent connects to cloud and on-prem tools
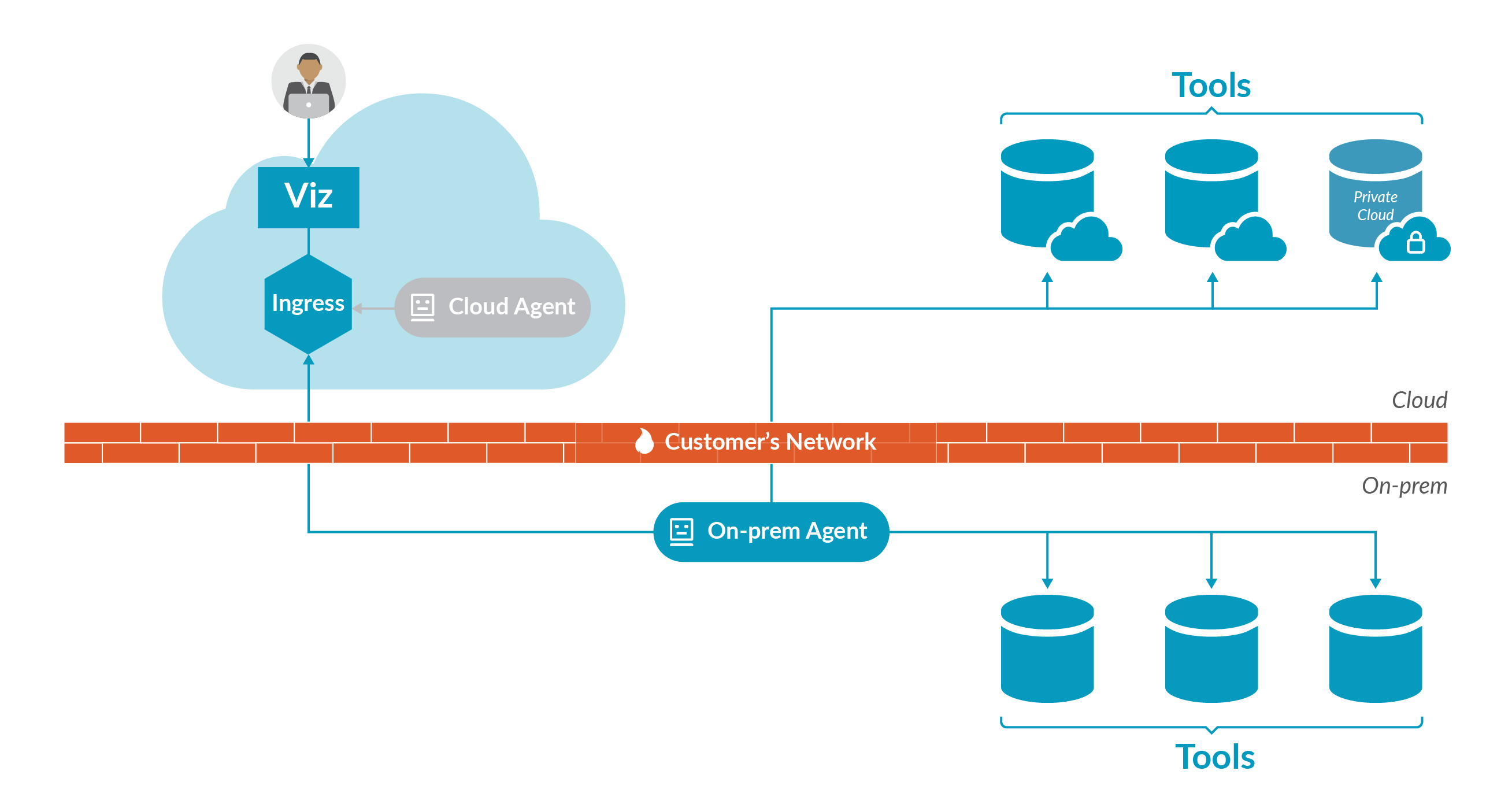
Diagram B shows a scenario where a customer may not be able to whitelist inbound IP addresses due to security or technical constraints. In that scenario, the on-prem agent can be used to access cloud repositories, and the firewall can be managed within the customer's own network.

