WhiteHat Sentinel
Last Updated:
Due to a change in WhiteHat's API, Planview Hub will be discontinuing support for URL-based verification and switching to API-based verification on February 15, 2022. As a result, you must upgrade to the latest version of Hub before the specified date to prevent breaking any existing WhiteHat integrations.

Overview
To mitigate security threats, you need to incorporate strong security practices into every phase of the software development and delivery process. The WhiteHat Sentinel connector does just that. It integrates best-of-breed ALM tools to secure and trace vulnerabilities across the SDLC. This allows software delivery professionals to collaborate while still working within their tools of choice.
For example:
- Let’s say the Chief Information Security Officer’s team uses WhiteHat Sentinel to monitor websites for vulnerabilities.
- When Sentinel detects one, the Sentinel connector automatically creates a defect in the specified tool the development team uses to track and manage defects.
- It then maintains synchronization between the vulnerability and defect. So when the developer fixes the defect, that information is immediately relayed back to Sentinel.
- This increases visibility and traceability, and assures that all vulnerabilities are traced and fixed.
Key Features and Benefits
- Synchronizes artifacts across the lifecycle, allowing information to flow freely between WhiteHat Sentinel and other tools
- Improve team collaboration by connecting WhiteHat Sentinel to third party tools and allowing artifacts to be synchronized across the lifecycle.
- Support cross-tool traceability and reporting, removing the need for manual processes and spreadsheets — supports real-time reporting of the status of security vulnerabilities and improves security and compliance by providing traceability between security vulnerabilities and their fixes
Example Use Case
-
New vulnerabilities from WhiteHat flow to Jira (or other purpose-built system) along with current status
- Once vulnerability is resolved in Jira, updated status flows to WhiteHat, and re-test in WhiteHat is invoked
-
If a resolved vulnerability gets reopened in WhiteHat, so does the corresponding Jira issue
Demo Videos
Connector Setup Details
This section describes the basic steps needed to prepare your WhiteHat Sentinel instance for use with Hub. Note that additional fields for synchronization or configuration of queries may be required depending on the requirements of your integration.
Minimal User Permissions & Hub User
We recommend that you create a new user within your external tool, to be used only for your Hub integration. This is the user information you will enter when setting up your repository connection within Planview Hub. By creating a new user, you will ensure that the correct permissions are granted, and allow for traceability of the modifications that are made by the synchronization.
In general, your user account should have sufficient permissions to create, read, and update artifacts in your repository. However, depending on the use case, your user may need different permissions. For example, if you are only interested in flowing data out of your repository, your user may not need to have full CRUD access, as the 'create' and 'update' permissions may not be needed.
Your user should have a secure password or token. Please be aware that Hub will not allow you to save a repository connection utilizing a weak password/token, such as 'tasktop.'
Request a new account in WhiteHat Sentinel through the WhiteHat Security Customer Success Center.
There are no minimal user permissions required for the WhiteHat Sentinel connector.
Connecting to the WhiteHat Repository
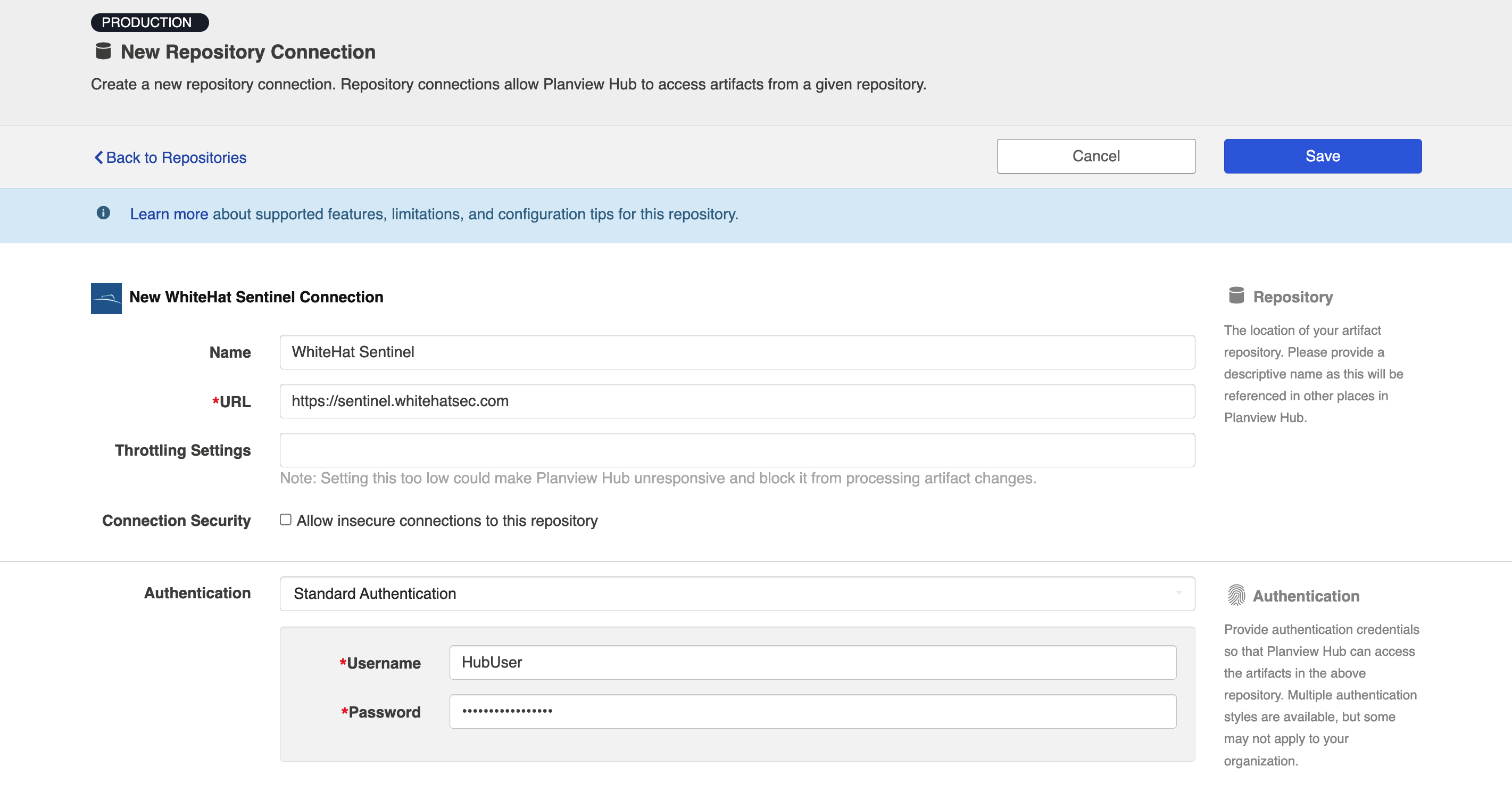
Standard Authentication
Required Fields:
- Location/Connection URL
- Example Format: https://sentinel.whitehatsec.com
- Username
- Password
Optional Fields:
- Throttling Settings: This field indicates the number of API calls that can be made per minute. See details here.
- Note: This field should only be set under the guidance of customer care as the ideal value is highly dependent on each customer's unique environment.
- Connection Security: If checked, insecure connections to this repository will be allowed. See details here.
Learn more about how to set up your repository in Planview Hub here.
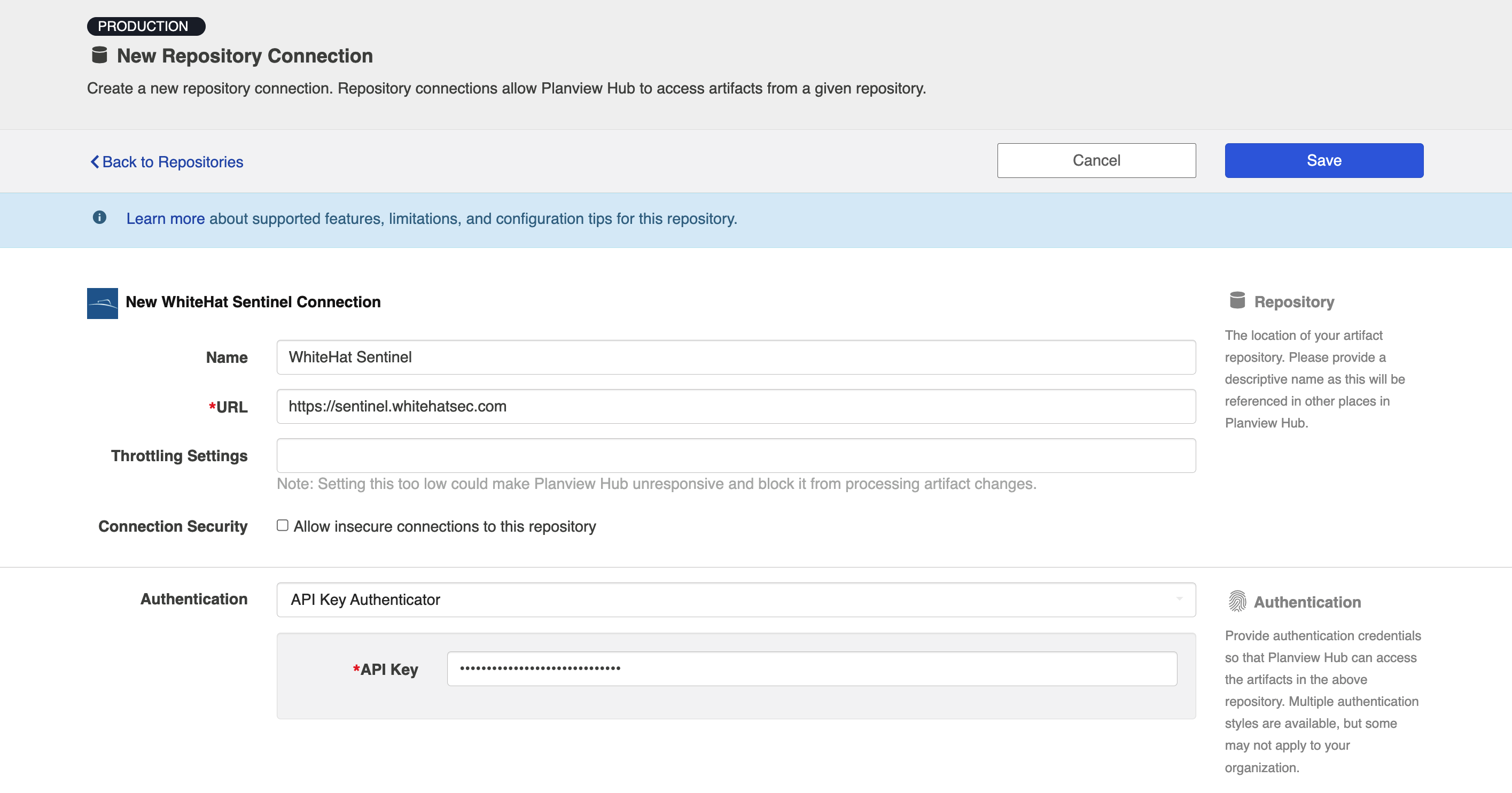
API Key Authenticator
Required Fields:
- Location/Connection URL
- Example Format: https://sentinel.whitehatsec.com
- API Key
- An API key associated with the WhiteHat account you'd like to use for your integration
- Contact WhiteHat support to learn how to set up an API key to use for your integration, or login through the WhiteHat Security Customer Success Center to access the resources in the Customer Portal.
Optional Fields:
- Throttling Settings: This field indicates the number of API calls that can be made per minute. See details here.
- Note: This field should only be set under the guidance of customer care as the ideal value is highly dependent on each customer's unique environment.
- Connection Security: If checked, insecure connections to this repository will be allowed. See details here.
SSO Authentication
Additionally, WhiteHat supports the following SSO implementations:
- Script (HTTP cookies)
- X.509 Certificate
Learn more about how to set up your repository in Planview Hub here.
Other Configuration Settings
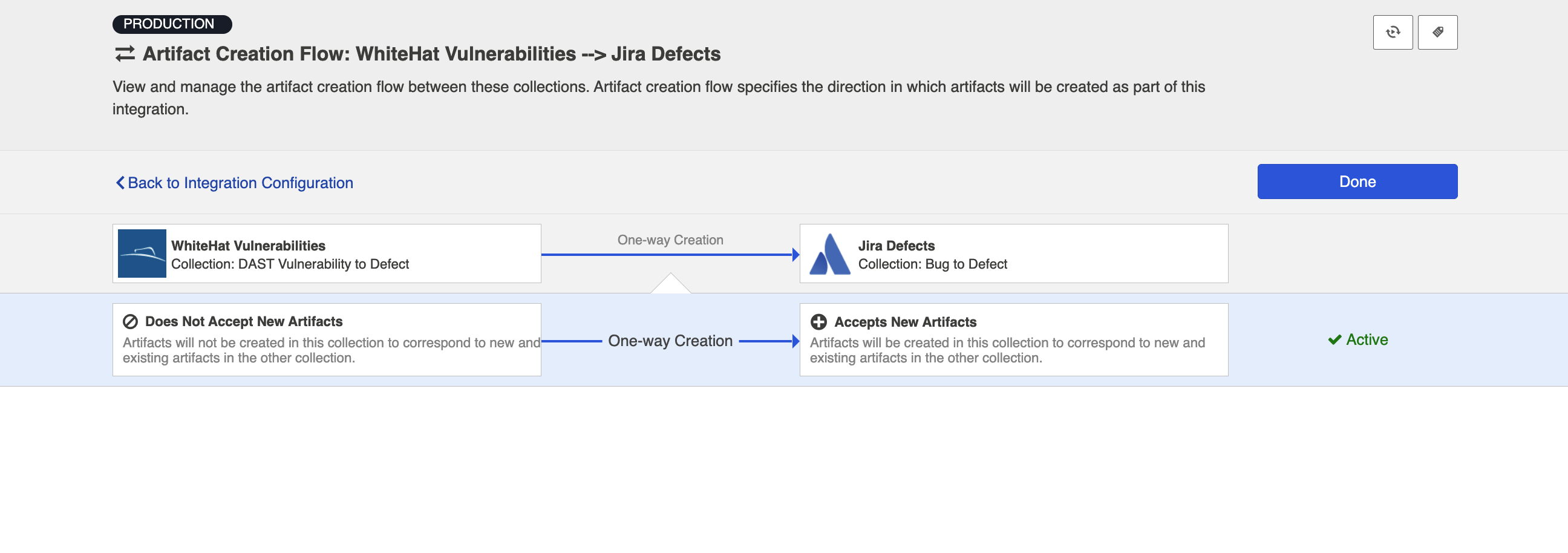
Artifact Creation Flow
As users cannot create artifacts (vulnerabilities) within WhiteHat Sentinel, the WhiteHat connector does not support artifact creation. As such, you will see that only one-way artifact creation (out of WhiteHat) can be configured from the Artifact Creation Flow screen:
Retesting Vulnerabilities
To retest DAST vulnerabilities, you will need to have a transition script as the transform from the model to the ‘Retest Vuln Status’ single select field.
Here is an example (where 'Send For Retest' is a select item in the “Retest Status’ field in the model):
function transitionArtifact(context, transitions) {
if (context.sourceArtifact. retest_status=== 'Send For Retest') {
return transitions[0];
}
}
Full Scan
Due to third party API limitations, changes to the following fields may not trigger change detection or cause a synchronization immediately. To ensure these updates synchronize, a high fidelity full scan must occur or another qualifying change must be made to the artifact:
- Description field
- Industry field
- Language field
Learn more about how to configure change detection and full scan intervals in Planview Hub here.
Supported Features
Special Features Supported
You can learn more about special features in Planview Hub here.
|
Feature |
Applicable Hub Versions |
Applicable Repository Versions |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Planview Hub: 17.3 and later |
Any supported repository version: |
|
|
|
|
Supported Artifact Types
Supported Work Items
Learn about the difference between containers and work items in Planview Hub here.
|
Supported Work Item Type |
Applicable Hub Versions |
Applicable Repository Versions |
Unique URL? |
|---|---|---|---|
|
DAST Vulnerability |
Planview Hub: 17.3 and later |
Any supported repository version: |
Yes |
|
SAST Vulnerability |
Planview Hub: 17.3 and later |
Any supported repository version: |
Yes |
Supported Containers
Learn more about containment in Planview Hub here.
|
Containers that can synchronize between repositories |
Applicable Hub Versions |
Applicable Repository Versions |
Unique URL? |
|---|---|---|---|
|
Asset (Application) Note: Beginning in Hub version 22.4, containers can be treated as work items. Learn more here. |
Planview Hub: 18.2 and later |
Any supported repository version: |
Yes |
|
Asset (Site) Note: Beginning in Hub version 22.4, containers can be treated as work items. Learn more here. |
Planview Hub: 18.2 and later |
Any supported repository version: |
Yes |
|
Containers used to define the boundary of a collection (When clicking 'Manage Projects' on a Collection) |
|
|
|
|
For SAST Vulnerability collections: Asset (Application) |
Planview Hub: 17.3 and later |
Any supported repository version: |
N/A |
|
for DAST Vulnerability collections: Asset (Site) |
Planview Hub: 17.3 and later |
Any supported repository version: |
N/A |
|
for Asset collections: Since assets do not have an enclosing container, a placeholder project called 'Not Applicable' must be selected. This means that the entire Whitehat repository will serve as your container. |
Planview Hub: 18.2 and later |
Any supported repository version: |
N/A |
|
Containers used for artifact routing |
|
|
|
|
Asset (Application) for SAST Vulnerability collections |
Planview Hub: 17.3 and later |
Any supported repository version: |
N/A |
|
Asset (Site) for DAST Vulnerability collections |
Planview Hub: 17.3 and later |
Any supported repository version: |
N/A |
Supported Field Types
Note: If one field of a given type is supported, others that are also that type in theory should also work. However, sometimes there are instances in which this is not the case due to the repository. So, while we can claim support for fields at the type level, there is a chance that some specific fields of a given type will not synchronize properly.
|
Standard Field Type |
Does Hub support custom fields of this type? |
How is field type referenced in the repository? |
Sample Repository Fields Supported |
Particular Repository Fields NOT Supported |
|---|---|---|---|---|
|
|
N/A |
|
All vulnerabilities: Vulnerability ID, Vulnerability Class, Status DAST vulnerabilities: Customized By, Custom Policy Description, Custom Policy Name, CVSS Vector, Mitigated By |
SAST vulnerabilities: Class |
|
|
N/A |
|
All vulnerabilities: Type DAST vulnerabilities: Service Level Abbreviation, Asset Name, Rating SAST vulnerabilities: Asset Name, Compliance, impact Readable, Likelihood Readable, WhiteHat Rating |
SAST vulnerabilities: Status Unpublished |
|
|
N/A |
|
DAST vulnerabilities/Assets: Tags |
|
|
|
N/A |
|
DAST vulnerabilities: Accepted, Has Notes, Mitigated SAST vulnerabilities: Is Locked, Manual, Remediation Available |
|
|
|
|
|
|
|
|
|
N/A |
|
All vulnerabilities: Closed, Opened On, Found, Modified, Opened DAST vulnerabilities: Customized On |
|
|
|
|
|
|
|
|
|
N/A |
|
DAST vulnerabilities: CVSS Score |
|
|
|
N/A |
|
All vulnerabilities: ID, Impact, Likelihood DAST vulnerabilities: Custom Risk, Score, Severity, Threat SAST vulnerabilities: Verified Patches Count |
SAST vulnerabilities: Application ID |
|
|
N/A |
|
All vulnerabilities: Endpoint, Location |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
N/A |
DAST Vulnerability, SAST Vulnerability |
All vulnerabilities: Description, Solution |
|
|
|
|
|
|
|
|
|
|
|
|
|
Functional Limitations
|
Category |
Limitation |
Applicable Hub Versions |
Applicable Repository Versions |
|---|---|---|---|
|
Third Party Functional Limitation |
Status Field Mappings The connector may return more artifacts than visible in the web UI. For example, vulnerabilities with the query status 'discovered' or 'false' may be returned, however, attempting to open these artifacts in Hub may not work. As a result, status field mappings will need to account for these status values or allow new values. |
Planview Hub: 17.3 and later |
Any supported repository version: |
|
Third Party Functional Limitation |
Assets Fields on assets are read only, with the exception of the 'tags' field, which can be updated. |
Planview Hub: 18.2 and later |
Any supported repository version: |
|
Third Party Functional Limitation |
Artifact Management WhiteHat has no artifact creation or deletion. |
Planview Hub: 17.3 and later |
Any supported repository version: |
|
Third Party Functional Limitation |
SAST Vulnerabilities SAST vulnerabilities have no writeable fields, and therefore cannot be updated. |
Planview Hub: 17.3 and later |
Any supported repository version: |
|
Third Party Functional Limitation |
Query Language Search WhiteHat does not support query-language search. |
Planview Hub: 17.3 and later |
Any supported repository version: |
|
Third Party Functional Limitation |
DAST Vulnerabilities Tags on DAST vulnerabilities cannot contain non-ASCII Unicode values, spaces, or dashes, and are limited to 25 chars. |
Planview Hub: 17.3 and later |
Any supported repository version: |
|
Third Party API Limitation |
SAST Vulnerabilities There are no repository queries available for SAST vulnerability collections. |
Planview Hub: 17.3 and later |
Any supported repository version: |
 Time Worked (Worklogs)
Time Worked (Worklogs)